Enhancing Security with faillock and fail2ban

Enhancing security in a Red Hat Enterprise Linux (RHEL) environment is crucial, and tools like faillock and fail2ban offer valuable features to mitigate unauthorized access attempts. In this guide, we’ll delve into the functionalities of these commands, their configurations, and when to use each for optimal security.
Understanding faillock
Features of faillock
faillock is a command-line utility in RHEL that tracks and manages failed login attempts. Here are its key features:
- Locking User Accounts: faillock can lock user accounts after a specified number of failed login attempts, preventing further login attempts.
- Displaying Lockout Information: It shows details about locked user accounts, including when the lockout occurred and how many failed attempts were made.
- Resetting Failures: Administrators can reset the failure count manually using the faillock command.
Using faillock
Locking and Unlocking User Accounts
To lock a user account after a certain number of failed attempts:
faillock --user <username> --lock
To unlock a previously locked user account:
faillock --user <username> --reset
Understanding fail2ban
Features of fail2ban
fail2ban is a more comprehensive solution that goes beyond locking user accounts. Its features include:
- Dynamic Firewall Rules: fail2ban dynamically updates firewall rules to block IP addresses of hosts exhibiting suspicious behavior.
- Multiple Service Support: It can monitor various services like SSH, FTP, and more, detecting and responding to suspicious activities across multiple services.
- Customizable Actions: Administrators can configure custom actions for different scenarios, such as banning IP addresses for a specific duration.
Using fail2ban
Installation and Configuration
- Installation: Install fail2ban using the package manager (yum or dnf):
sudo dnf install fail2ban -yThe
EPEL repositorymust be installed/configured in order to installfail2ban. You may download the EPEL repository by running the following commands :
sudo dnf install https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rpm -y
- Configuration: Configure fail2ban by editing the
jail.conffile located in/etc/fail2ban/. Customize settings such as ban duration, threshold for failed attempts, and more. - Starting fail2ban: Start the fail2ban service:
sudo systemctl start fail2ban
Automatic IP Ban Example
To automatically ban an IP address after 3 failed login attempts, configure a jail in the jail.conf file:
This configuration seems to be designed to drop connections or packets from an offending IP address. Add the below to the top of the config file, after the initial set of commented information :
[blocktype]
returntype = DROP
action = %(action_)s[blocktype=%(blocktype)s,returntype=%(returntype)s, actionstart_on_demand=false, actionrepair_on_unban=true]
bantime = 1h
maxretry = 1
findtime = 1
| Parameter | Description |
|---|---|
| [blocktype] | Section header defining a jail for a particular type of block or behavior. |
| returntype | Specifies the action taken when a match is found. Here it’s set to DROP, meaning packets from the banned IP will be dropped. |
| action | Defines the action parameters for the jail, including banning an IP and including specific metadata about the ban. |
| bantime | Sets the duration an IP address will be banned after reaching the maxretry limit. Set here to 1 hour (1h). |
| maxretry | Specifies the number of failures or matches within the findtime before an action is taken. Set to 1. |
| findtime | Defines the time window within which maxretry failures or matches are counted. Set to 1 (possibly 1 second or 1 minute). |
Then we will add the below to the bottom of the config file :
[automatic-ban]
enabled = true
filter = <filter-name>
action = iptables[name=<filter-name>, port=<port>, protocol=<protocol>]
logpath = <path/to/logfile>
maxretry = 3
bantime = 3600
Replace filter-name, port, protocol, and path/to/logfile with appropriate values for your system.
This configuration will monitor the /var/log/secure log file for SSH-related authentication failure events (using the sshd filter). If an IP address fails to authenticate three times within the specified time frame, Fail2Ban will block access to the SSH port for that IP address for one hour using an IPTables rule (iptables action).
Below is an example using sample/default information for configuring a fail2ban jail in the jail.conf configuration file :
[automatic-ban]
enabled = true
filter = sshd
action = iptables[name=automatic-ban, port=ssh, protocol=tcp]
logpath = /var/log/secure
maxretry = 3
bantime = 3600
Always ensure the logpath points to the correct log file for the service you intend to monitor. Customize the maxretry (number of allowed failed attempts) and bantime (ban duration) based on your security requirements.
| Parameter | Description |
|---|---|
| [automatic-ban] | Section header defining the jail. |
| enabled = true | Indicates that this jail is active and will be used by Fail2Ban to monitor and respond to incoming events. |
| filter = sshd | Specifies the filter to be used for this jail, filtering the SSH service using the sshd filter. |
| action = iptables[name=automatic-ban, port=ssh, protocol=tcp] | Defines the action taken when a match is found, adding an IPTables rule to block SSH access for a defined duration. |
| logpath = /var/log/secure | Specifies the log file path to monitor for patterns defined in the sshd filter. |
| maxretry = 3 | Sets the maximum number of retries or failed login attempts allowed before triggering the defined action. |
| bantime = 3600 | Defines the duration for which an IP address will be banned (in seconds). |
After making changes in the jail.conf file, remember to restart fail2ban for the configurations to take effect:
sudo systemctl restart fail2ban
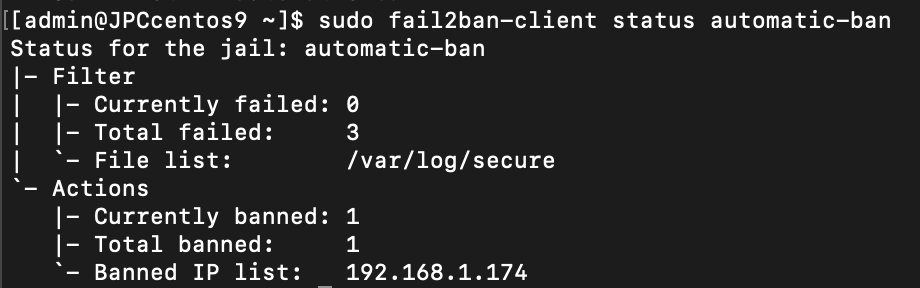
How to Confirm an IP Address Ban
If you suspect that an IP address is banned, do the following to confirm
sudo fail2ban-client status <name_of_jail>
In this example the name of the jail is automatic-ban so the command would be
sudo fail2ban-client status automatic-ban
This commnand will display various information about the ban, including how many IPs are currently banned and a list of all IPs that are banned.
How to Remove an IP Address Ban
To remove an IP Address ban, run the below command. Once this command is executed properly, the ban will be removed and you will be able to successfully ssh into that machine/server again from that IP address.
sudo fail2ban-client set automatic-ban unbanip 192.168.1.174
When to Use Each Command
faillockis suitable for managing user account lockouts and tracking individual user login failures.fail2banis more extensive, providing protection against various types of attacks by dynamically banning potential malicious hosts.
Conclusion
In RHEL, faillock and fail2ban are powerful tools to bolster system security. While faillock focuses on managing user account lockouts, fail2ban offers a broader approach, protecting against multiple types of attacks by dynamically updating firewall rules.
For detailed configurations and advanced settings, refer to the official RHEL documentation. Implement these tools to fortify your system against unauthorized access attempts and enhance overall security.
📝 For more detailed instructions and information, you can refer to the official Faillock documentation and the Fail2ban documentation.